Data Engineering Integration
- Data Engineering Integration H2L
- All Products

Property
| Description
|
|---|---|
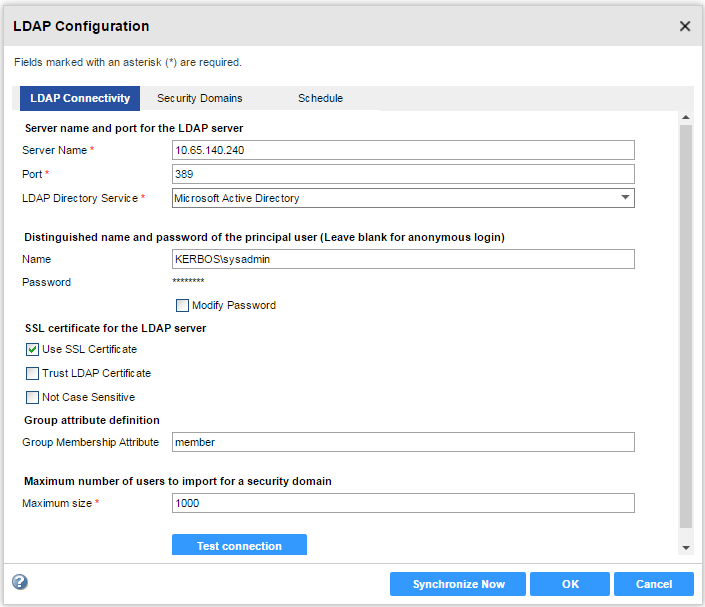
Server Name
| Host name or IP address of the Active Directory server.
|
Port
| Listening port for the Active Directory server. The default value is 389.
|
LDAP Directory Service
| Select Microsoft Active Directory.
|
Name
| Distinguished name (DN) for the principal LDAP user. The user name often consists of a common name (CN), an organization (O), and a country (C). The principal user name is an administrative user with access to the directory. Specify a user that has permission to read other user entries in the directory service.
|
Password
| Password for the principal LDAP user.
|
Use SSL Certificate
| Indicates that the LDAP server uses the Secure Socket Layer (SSL) protocol.
If the LDAP server uses SSL, you must import the certificate into a truststore file on every gateway node within the Informatica domain. You must also set the INFA_TRUSTSTORE and INFA_TRUSTSTORE_PASSWORD environment variables if you do not import the certificate into the default Informatica truststore.
|
Trust LDAP Certificate
| Determines whether the Service Manager can trust the SSL certificate of the LDAP server. If selected, the Service Manager connects to the LDAP server without verifying the SSL certificate. If not selected, the Service Manager verifies that the SSL certificate is signed by a certificate authority before connecting to the LDAP server.
|
Not Case Sensitive
| Indicates that the Service Manager must ignore case sensitivity for distinguished name attributes when assigning users to groups. Enable this option.
|
Group Membership Attribute
| Name of the attribute that contains group membership information for a user. This is the attribute in the LDAP group object that contains the distinguished names (DNs) of the users or groups who are members of a group. For example,
member or
memberof .
|
Maximum size
| Maximum number of user accounts to import into a security domain.
If the number of user to be imported exceeds the value for this property, the Service Manager generates an error message and does not import any user. Set this property to a higher value if you have many users to import.
The default value is 1000.
|
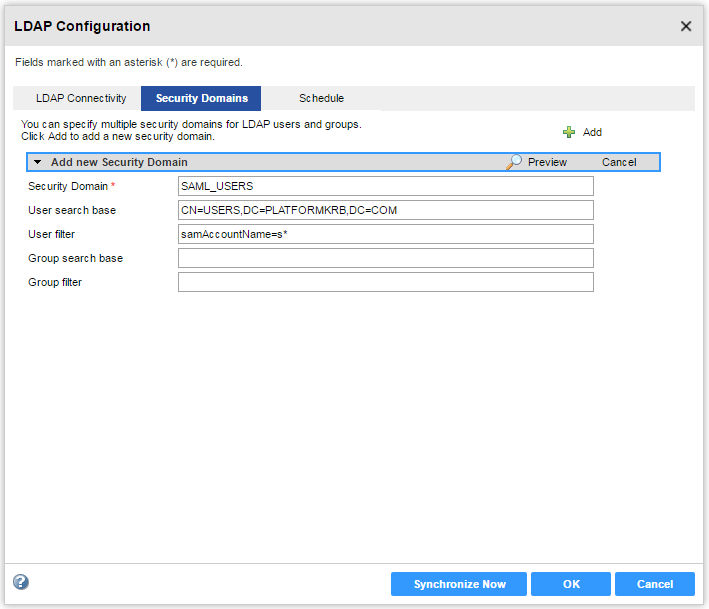
Property
| Description
|
|---|---|
Security Domain
| Name of the LDAP security domain. The name is not case sensitive and must be unique within the domain. The name cannot exceed 128 characters or contain the following special characters:
, + / < > @ ; \ % ?
The name can contain an ASCII space character except for the first and last character. All other space characters are not allowed.
|
User search base
| Distinguished name (DN) of the entry that serves as the starting point to search for user names in the LDAP directory service. The search finds an object in the directory according to the path in the distinguished name of the object.
In Active Directory, the distinguished name of a user object might be cn=UserName,ou=OrganizationalUnit,dc=DomainName, where the series of relative distinguished names denoted by dc=DomainName identifies the DNS domain of the object.
For example, to search the Users container that contains user accounts in the example.com Windows domain, specify CN=USERS,DC=EXAMPLE,DC=COM.
|
User filter
| An LDAP query string that specifies the criteria for searching for users in Active Directory. The filter can specify attribute types, assertion values, and matching criteria.
For Active Directory, format the query sting as:
sAMAccountName=<account> |
Group search base
| Distinguished name (DN) of the entry that serves as the starting point to search for group names in Active Directory.
|
Group filter
| An LDAP query string that specifies the criteria for searching for groups in the directory service.
|