Administrator
- Administrator
- All Products

<Secure Agent installation directory>/apps/process-engine/conf/certs
<Secure Agent installation directory>/apps/process-engine/conf
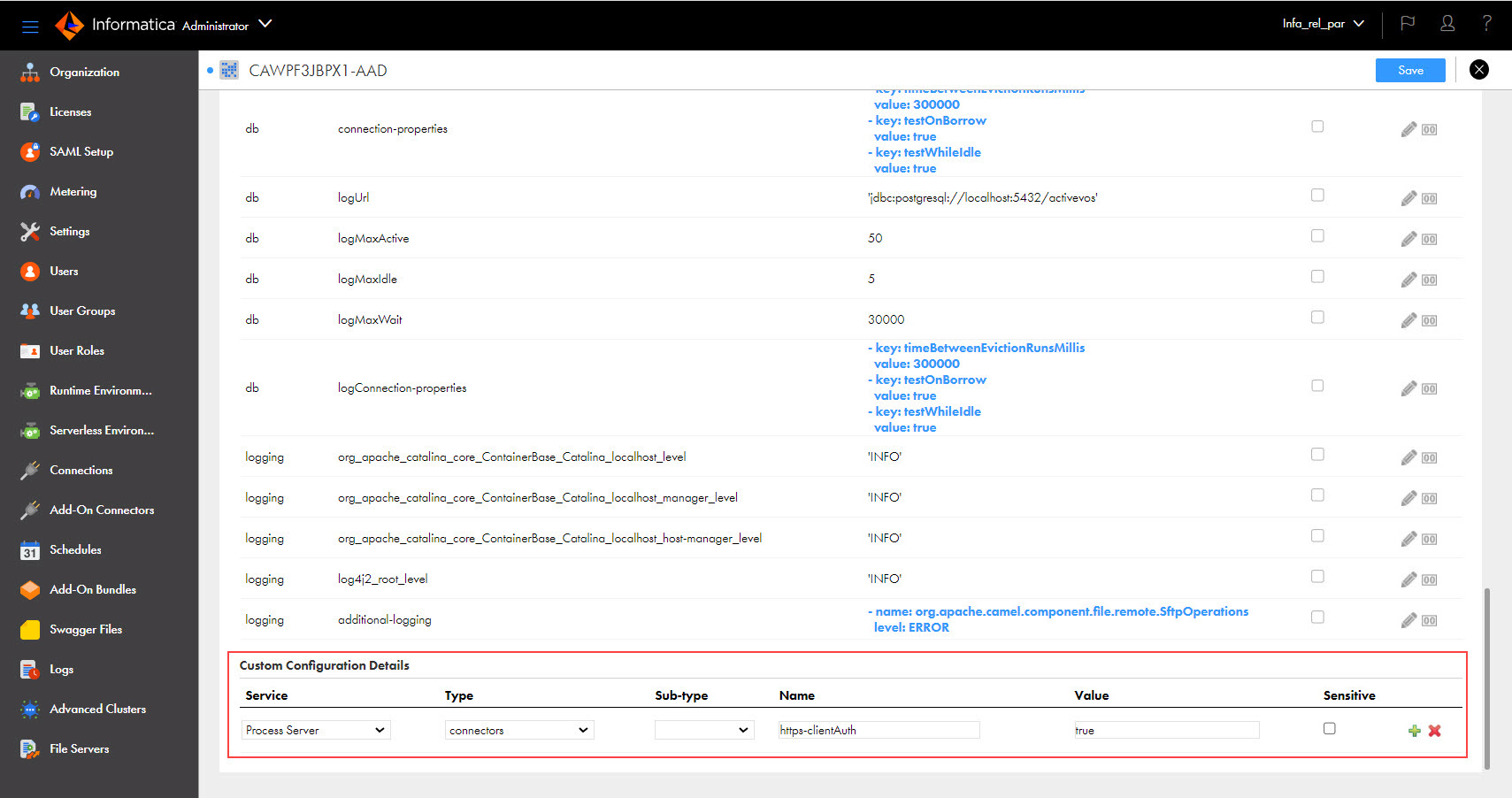
<Secure Agent installation directory>/downloads/package-process-engine.<latest_version>/package/app/conf/