Data Engineering Integration
- Data Engineering Integration 10.5
- All Products

spark.hadoop.fs.s3a.server-side-encryption-algorithm AES256
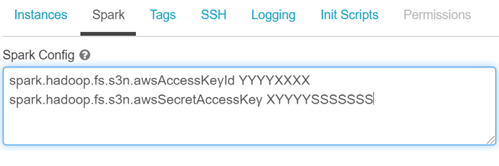
spark.hadoop.fs.s3n.awsAccessKeyld YYYYXXXX spark.hadoop.fs.s3n.awsSecretAccessKey XYYYYSSSSSSS spark.hadoop.fs.s3a.server-side-encryption-algorithm AES256
spark.hadoop.fs.s3a.server-side-encryption-kms-master-key-id arn:aws:kms:us-west-XXXXX:key/XXXYYYYYYYYYYYYYYYYY spark.hadoop.fs.s3a.server-side-encryption-algorithm aws:kms spark.hadoop.fs.s3a.impl com.data bricks.s3a.S3AFileSystem
spark.hadoop.fs.s3n.awsAccessKeyld YYYYXXXX spark.hadoop.fs.s3n.awsSecretAccessKey XYYYYSSSSSSS spark.hadoop.fs.s3a.server-side-encryption-kms-master-key-id arn:aws:kms:us-west-XXXXX:key/XXXYYYYYYYYYYYYYYYYY spark.hadoop.fs.s3a.server-side-encryption-algorithm aws:kms spark.hadoop.fs.s3a.impl com.data bricks.s3a.S3AFileSystem