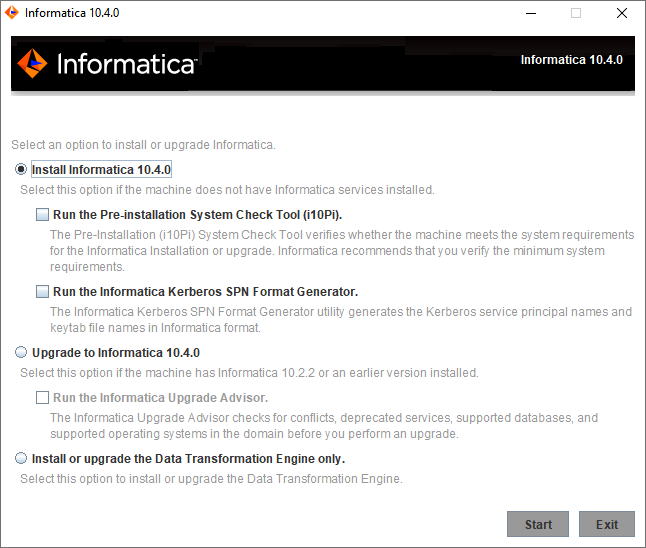
PowerCenter
- PowerCenter 10.4.0
- Tous les produits


Property
| Description
|
|---|---|
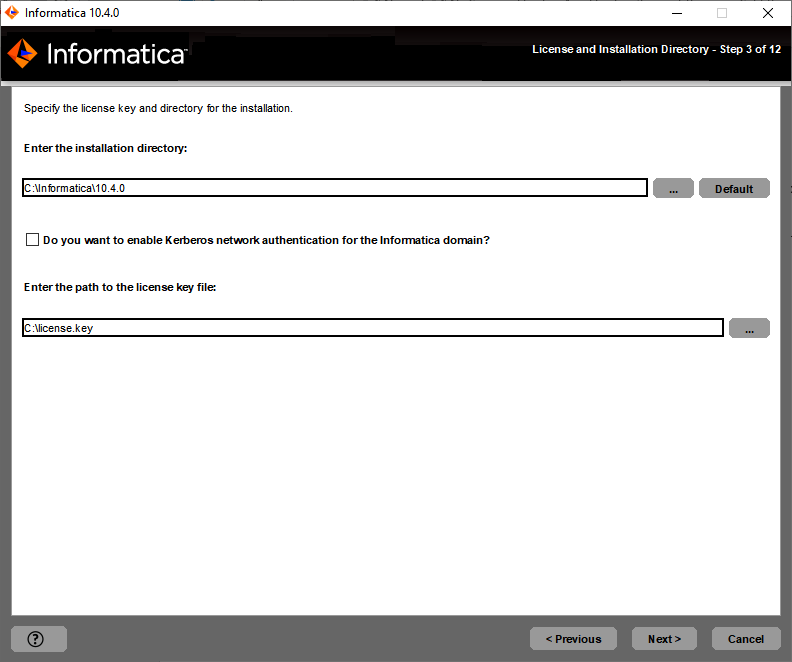
License key file
| Path and file name of the Informatica license key.
|
Installation directory
| Absolute path for the installation directory. The installation directory must be on the machine where you are installing Informatica. The directory names in the path must not contain spaces or the following special characters:
@ | * $ # ! % ( ) { } [ ]
Informatica recommends using alphanumeric characters in the installation directory path. If you use a special character such as á or €, unexpected results might occur at run time.
|

Niveau
| Description
|
|---|---|
Niveau processus
| Configure le domaine pour utiliser un nom de principal de service (SPN) et un fichier Keytab uniques pour chaque nœud et chaque service d'application sur un nœud.
Le nombre de SPN et de fichiers Keytab requis pour chaque nœud dépend du nombre de processus de service d'application exécutés sur le nœud. Utilisez l'option de niveau de processus pour les domaines qui nécessitent un niveau élevé de sécurité, comme par exemple les domaines de production.
|
Niveau nœud
| Configure le domaine pour partager les SPN et les fichiers keytab sur un nœud.
Cette option nécessite un SPN et un fichier Keytab pour le nœud et tous les services d'application exécutés sur le nœud. Elle requiert également un autre SPN et un autre fichier keytab pour tous les processus HTTP s'exécutant sur le nœud.
Utilisez l'option de niveau de nœud pour les domaines qui n'ont pas besoin d'un niveau élevé de sécurité, tels que les domaines de test et de développement.
|

Property
| Description
|
|---|---|
Domain name
| Name of the domain to create.
The name must not exceed 128 characters and must be 7-bit ASCII only. The name cannot contain a space or any of the following characters:
` % * + ; " ? , < > \ /
|
Node name
| Name of the node to create.
|
Node host name
| Fully qualified host name or IP address of the machine on which to create the node.
The node host name cannot contain the underscore (_) character. Do not use localhost. The host name must explicitly identify the machine.
|
Property
| Description
|
|---|---|
Service realm name
| Name of the Kerberos realm that the domain uses to authenticate users. The realm name must be in uppercase and is case-sensitive.
To configure Kerberos cross realm authentication, specify the name of each Kerberos realm that the domain uses to authenticate users, separated by a comma. For example:
COMPANY.COM,EAST.COMPANY.COM,WEST.COMPANY.COM
Use an asterisk as a wildcard character before a realm name to include all realms that include the name. For example:
*EAST.COMPANY.COM
|
User realm name
| Name of the Kerberos realm that the domain uses to authenticate users. The realm name must be in uppercase and is case-sensitive.
To configure Kerberos cross realm authentication, specify the name of each Kerberos realm that the domain uses to authenticate users, separated by a comma. For example:
COMPANY.COM,EAST.COMPANY.COM,WEST.COMPANY.COM
Use an asterisk as a wildcard character before a realm name to include all realms that include the name. For example:
*EAST.COMPANY.COM
|
Keytab directory
| Directory where all keytab files for the Informatica domain are stored. The name of a keytab file in the Informatica domain must follow a format set by Informatica.
|
Kerberos configuration file
| Path and file name of the Kerberos configuration file. Informatica requires the following name for the Kerberos configuration file:
krb5.conf |

Property
| Description
|
|---|---|
Enable HTTPS for Informatica Administrator
| Select this option to secure the connection to Informatica Administrator. To use an unsecure HTTP connection, clear the option.
By default, if secure communication is enabled for the domain, the installer enables this option. You can also enable this option even if you do not enable secure communication for the domain.
|
Port
| The port to use for communication between Informatica Administrator and the Service Manager.
|
Use a keystore file generated by the installer
| Use a self-signed keystore file generated by the installer. The installer creates a keystore file named Default.keystore in the following location:
<Informatica installation directory>\tomcat\conf\
|
Specify a keystore file and password
| Use a keystore file that you create. You can use a keystore file with a self-signed certificate or a certificate signed by a certification authority.
|
Keystore password
| A plain-text password for the keystore file. Required if you use a keystore file that you create.
|
Keystore file
| Path and file name of the keystore file. Required if you use a keystore file that you create.
|

Option
| Description
|
|---|---|
Use the default Informatica SSL certificate file.
| Select to use the default Informatica truststore file for SAML authentication.
|
Enter the location of the SSL certificate file.
| Select to use a custom truststore file for SAML authentication. Specify the directory containing the custom truststore file on gateway nodes within the domain. Specify the directory only, not the full path to the file.
|
Property
| Description
|
|---|---|
Truststore Directory
| Specify the directory containing the custom truststore file on gateway nodes within the domain. Specify the directory only, not the full path to the file.
|
Truststore Password
| The password for the custom truststore file.
|

Option
| Description
|
|---|---|
Use the default Informatica SSL certificate files
| Use the default SSL certificates provided by Informatica.
If you do not provide an SSL certificate, Informatica uses the same default private key for all Informatica installations. If you use the default Informatica keystore and truststore files, the security of your domain could be compromised. To ensure a high level of security for the domain, select the option to specify the location of the SSL certificate files.
|
Specify the location of the SSL certificate files
| Use SSL certificates that you provide. You must specify the location of the keystore and truststore files.
You can provide a self-signed certificate or a certificate issued by a certificate authority (CA). You must provide SSL certificates in PEM format and in Java Keystore (JKS) files. Informatica requires specific names for the SSL certificate files for the Informatica domain. You must use the same SSL certificates for all nodes in the domain. Store the truststore and keystore files in a directory accessible to all the nodes in the domain and specify the same keystore file directory and truststore file directory for all nodes in the same domain.
|
Property
| Description
|
|---|---|
Keystore file directory
| Directory that contains the keystore files. The directory must contain files named infa_keystore.jks and infa_keystore.pem.
|
Keystore password
| Password for the keystore infa_keystore.jks.
|
Truststore file directory
| Directory that contains the truststore files. The directory must contain files named infa_truststore.jks and infa_truststore.pem.
|
Truststore password
| Password for the infa_truststore.jks file.
|
Property
| Description
|
|---|---|
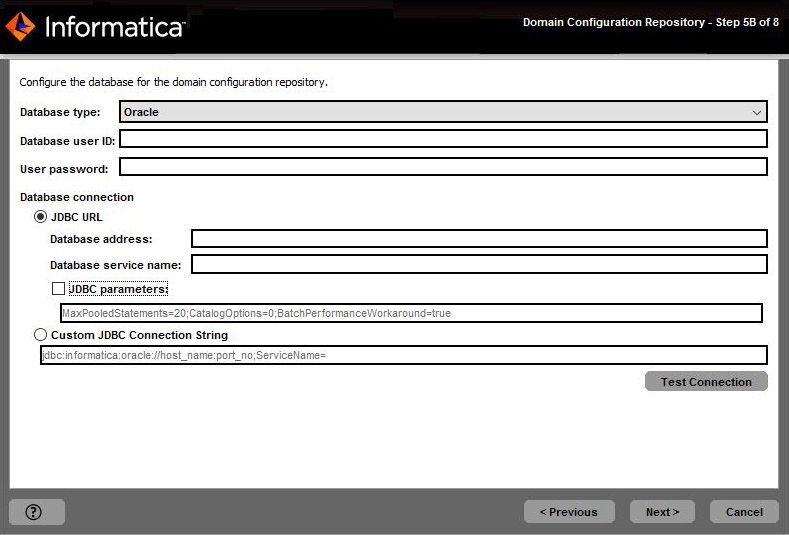
Database type
| Database for the repository. Select one of the following databases:
|
Database user ID
| User account for the repository database.
|
User password
| Password for the database user account.
|
Property
| Description
|
|---|---|
Tablespace
| Name of the tablespace in which to create the tables. Specify a tablespace that meets the pageSize requirement of 32768 bytes.
In a single partition database, if this option is not selected, the installer creates the tables in the default tablespace.
In a multipartition database, select this option and specify the name of the tablespace that resides in the catalog partition of the database.
|
Property
| Description
|
|---|---|
Schema name
| Name of the schema that will contain the repository tables. If not selected, the installer creates the tables in the default schema.
|
Trusted connection
| Indicates whether to connect to Microsoft SQL Server through a trusted connection. Trusted authentication uses the security credentials of the current user to make the connection to Microsoft SQL Server. If not selected, the installer uses Microsoft SQL Server authentication.
|
Property
| Description
|
|---|---|
Database address
| Host name and port number for the database in the format
host_name:port .
|
Database service name
| Service or database name :
|
JDBC parameters
| Optional parameters to include in the database connection string. Use the parameters to optimize database operations for the database. Verify that the parameter string is valid. The installer does not validate the parameter string before it adds the string to the JDBC URL. If not selected, the installer creates the JDBC URL string without additional parameters.
|
Property
| Description
|
|---|---|
Database truststore file
| Path and file name of the truststore file for the secure database.
|
Database truststore password
| Password for the truststore file.
|
Custom JDBC Connection String
| JDBC connection string to connect to the secure database, including the host name and port number and the security parameters for the database.
|
Property
| Description
|
|---|---|
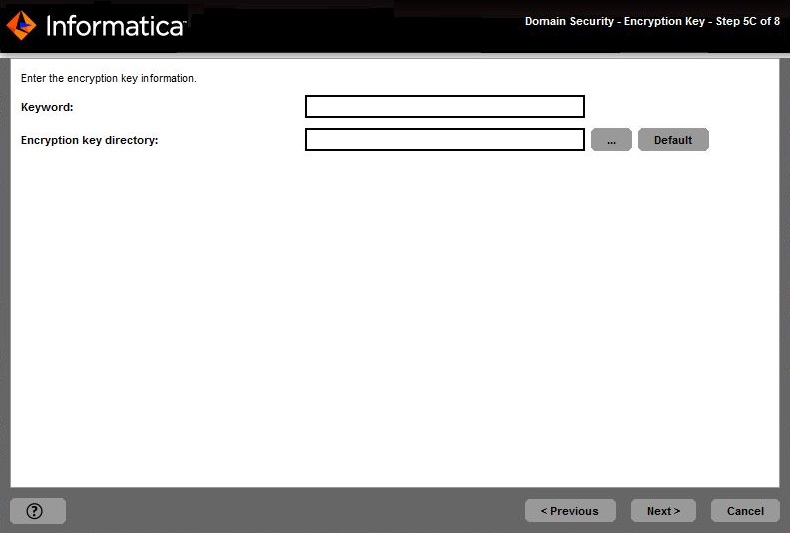
Keyword
| Keyword to use to create a custom encryption key to secure sensitive data in the domain. The keyword must meet the following criteria:
|
Encryption key directory
| Directory in which to store the encryption key for the domain. By default, the encryption key is created in the following directory:
<Informatica installation directory>/isp/config/keys .
|

Property
| Description
|
|---|---|
Domain name
| Name of the Informatica domain to create. The default domain name is Domain_<MachineName>.
The name must not exceed 128 characters and must be 7-bit ASCII only. The name cannot contain a space or any of the following characters:
` % * + ; " ? , < > \ /
|
Node name
| Name of the node to create.
|
Node host name
| Host name or IP address of the machine on which to create the node.
If the machine has a single network name, use the default host name. If the a machine has multiple network names, you can modify the default host name to use an alternate network name.
The node host name cannot contain the underscore (_) character. Do not use localhost. The host name must explicitly identify the machine.
|
Node port number
| Port number for the node. The default port number for the node is 6005. If the port number is not available on the machine, the installer displays the next available port number.
|
Domain user name
| User name for the domain administrator. You can use this user name to initially log in to Informatica Administrator. Use the following guidelines:
|
Domain password
| Password for the domain administrator. The password must be more than 2 characters and must not exceed 16 characters.
Not available if you configure the Informatica domain to run on a network with Kerberos authentication.
|
Confirm password
| Enter the password again to confirm.
Not available if you configure the Informatica domain to run on a network with Kerberos authentication.
|

Port
| Description
|
|---|---|
Service Manager port
| Port number used by the Service Manager on the node. The Service Manager listens for incoming connection requests on this port. Client applications use this port to communicate with the services in the domain. The Informatica command line programs use this port to communicate to the domain. This is also the port for the SQL data service JDBC/ODBC driver. Default is 6006.
|
Service Manager Shutdown port
| Port number that controls server shutdown for the domain Service Manager. The Service Manager listens for shutdown commands on this port. Default is 6007.
|
Informatica Administrator port
| Port number used by Informatica Administrator. Default is 6008.
|
Informatica Administrator HTTPS port
| No default port. Enter the required port number when you create the service. Setting this port to 0 disables an HTTPS connection to the Administrator tool.
|
Informatica Administrator shutdown port
| Port number that controls server shutdown for Informatica Administrator. Informatica Administrator listens for shutdown commands on this port. Default is 6009.
|
Minimum port number
| Lowest port number in the range of dynamic port numbers that can be assigned to the application service processes that run on this node. Default is 6014.
|
Maximum port number
| Highest port number in the range of dynamic port numbers that can be assigned to the application service processes that run on this node. Default is 6114.
|

Property
| Description
|
|---|---|
Run Informatica under a different user account
| Indicates whether to run the Windows service under a different user account.
|
User name
| User account with which to run the Informatica Windows service.
Use the following format:
<domain name>\<user account> This user account must have the Act as operating system permission.
|
Password
| Password for the user account with which to run the Informatica Windows service.
|

Property
| Description
|
|---|---|
Database type
| Database for the repository. Select one of the following databases:
|
Database user ID
| User account for the repository database.
|
User password
| Password for the database user account.
|
Property
| Description
|
|---|---|
Tablespace
| Name of the tablespace in which to create the tables. Specify a tablespace that meets the pageSize requirement of 32768 bytes.
In a single partition database, if this option is not selected, the installer creates the tables in the default tablespace.
In a multipartition database, select this option and specify the name of the tablespace that resides in the catalog partition of the database.
|
Property
| Description
|
|---|---|
Schema name
| Name of the schema that will contain the repository tables. If not selected, the installer creates the tables in the default schema.
|
Trusted connection
| Indicates whether to connect to Microsoft SQL Server through a trusted connection. Trusted authentication uses the security credentials of the current user to make the connection to Microsoft SQL Server. If not selected, the installer uses Microsoft SQL Server authentication.
|
Property
| Description
|
|---|---|
Database address
| Host name and port number for the database in the format
host_name:port .
|
Database service name
| Service or database name :
|
JDBC parameters
| Optional parameters to include in the database connection string. Use the parameters to optimize database operations for the database. Verify that the parameter string is valid. The installer does not validate the parameter string before it adds the string to the JDBC URL. If not selected, the installer creates the JDBC URL string without additional parameters.
|
Property
| Description
|
|---|---|
Database truststore file
| Path and file name of the truststore file for the secure database.
|
Database truststore password
| Password for the truststore file.
|
Custom JDBC Connection String
| JDBC connection string to connect to the secure database, including the host name and port number and the security parameters for the database.
|

Port
| Description
|
|---|---|
Model Repository Service name
| Name of the Model Repository Service to create in the Informatica domain.
|
Data Integration Service name
| Name of the Data Integration Service to create in the Informatica domain.
|
HTTP protocol type
| Type of connection to the Data Integration Service. Select one of the following options:
|
HTTP port
| Port number to used for the Data Integration Service. Default is 6030.
|
Option
| Description
|
|---|---|
Use the default Informatica SSL certificate files
| Use the default SSL certificates provided by Informatica.
If you do not provide an SSL certificate, Informatica uses the same default private key for all Informatica installations. If you use the default Informatica keystore and truststore files, the security of your domain could be compromised. To ensure a high level of security for the domain, select the option to specify the location of the SSL certificate files.
|
Enter the location of the SSL certificate files
| Use SSL certificates that you provide. You must specify the location of the keystore and truststore files.
|
Property
| Description
|
|---|---|
Keystore file
| Required. Path and file name of the keystore file that contains the private keys and SSL certificates for the database.
|
Keystore password
| Required. Password for the keystore file for the secure database.
|
Truststore file
| Required. Path and file name of the truststore file that contains the public key for the database.
|
Truststore password
| Required. Password for the truststore file for the secure database.
|