- Administrator H2L
- All Products

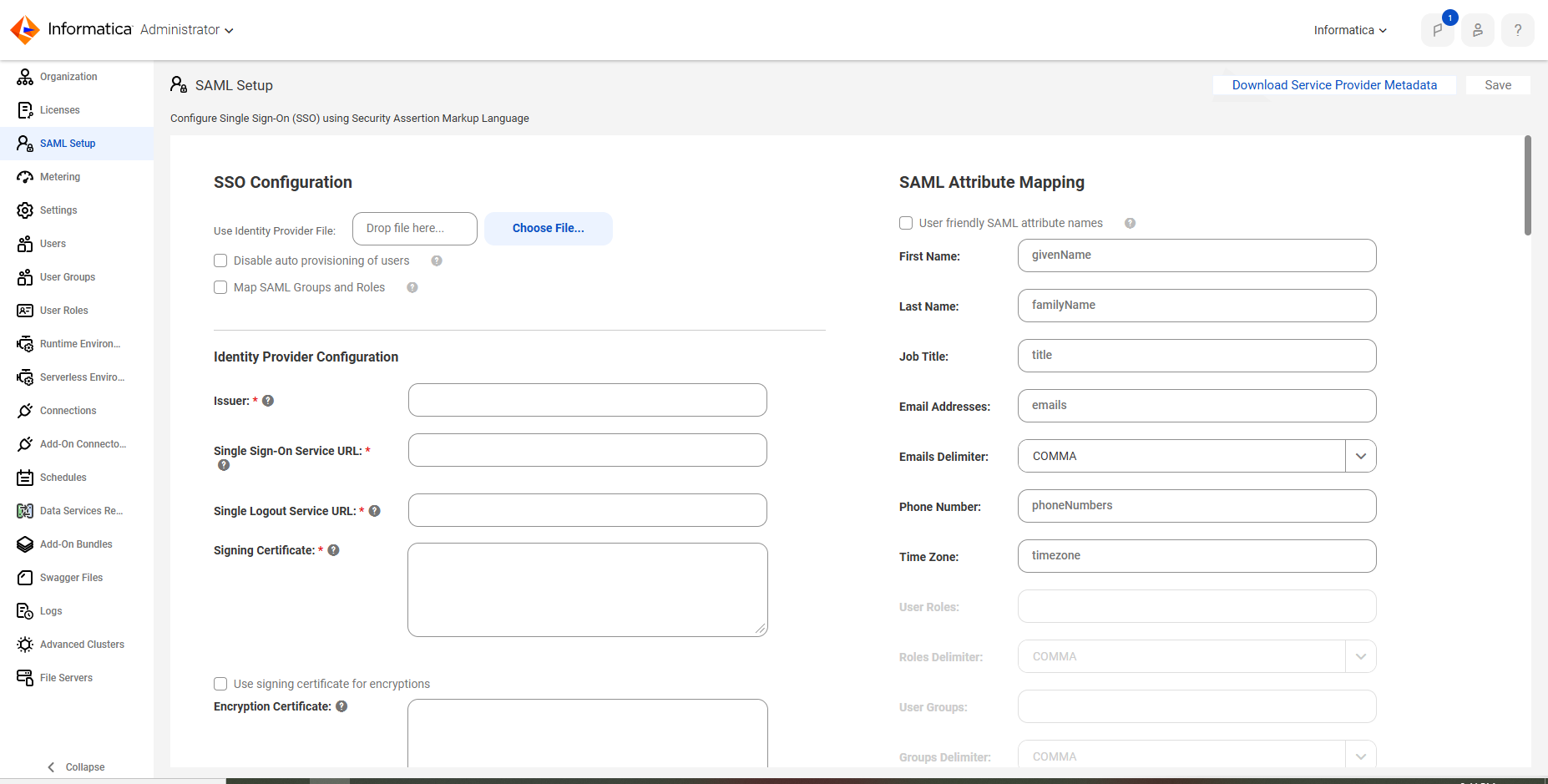
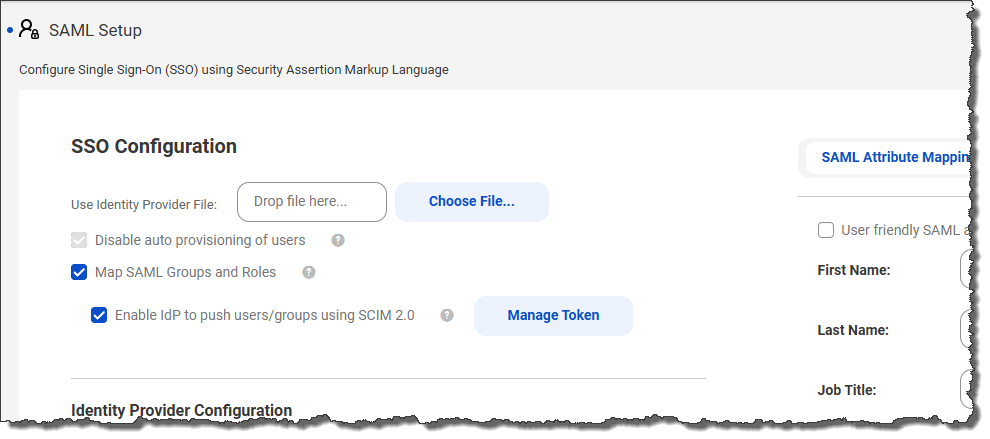
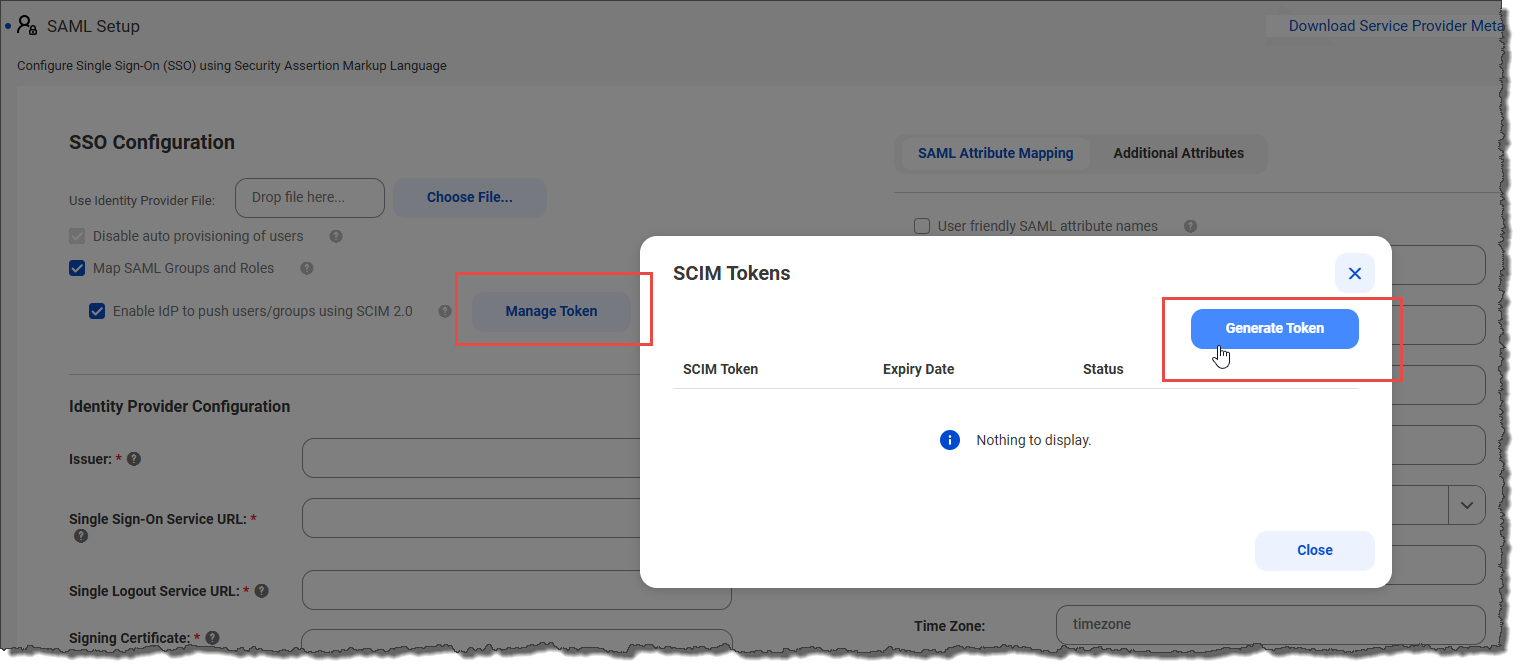
For step 5, I see the token is valid for 6 months. After that, will another token be required for an existing SCIM connection that has already been setup and working for 6 months? In other words, is the token like a password that expires after 6 months and must be reset?
Hi Karl,
Thanks for reaching out! We're currently checking this with our development & QA teams and will get back to you.
Hi again Karl,
We've confirmed with our QA team that the SCIM token is valid for 6 months. After that, yes, another token is required.
We'll clarify this in the documentation. Thanks for bringing this to our attention.