Dynamic Data Masking
- Dynamic Data Masking 9.9.2
- All Products


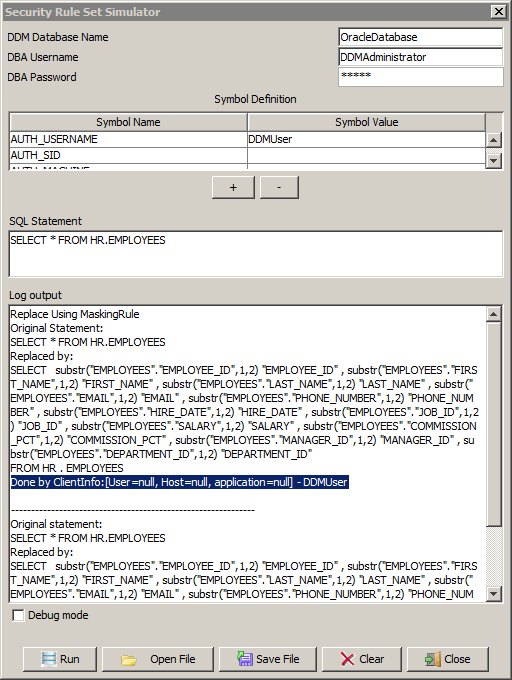
Replace Using MaskingRule Original Statement: SELECT * FROM HR.EMPLOYEES Replaced by: SELECT substr("EMPLOYEES"."EMPLOYEE_ID",1,2) "EMPLOYEE_ID" , substr("EMPLOYEES"."FIRST_NAME",1,2) "FIRST_NAME" , substr("EMPLOYEES"."LAST_NAME",1,2) "LAST_NAME" , substr("EMPLOYEES"."EMAIL",1,2) "EMAIL" , substr("EMPLOYEES"."PHONE_NUMBER",1,2) "PHONE_NUMBER" , substr("EMPLOYEES"."HIRE_DATE",1,2) "HIRE_DATE" , substr("EMPLOYEES"."JOB_ID",1,2) "JOB_ID" , substr("EMPLOYEES"."SALARY",1,2) "SALARY" , substr("EMPLOYEES"."COMMISSION_PCT",1,2) "COMMISSION_PCT" , substr("EMPLOYEES"."MANAGER_ID",1,2) "MANAGER_ID" , substr("EMPLOYEES"."DEPARTMENT_ID",1,2) "DEPARTMENT_ID" FROM HR . EMPLOYEES Done by ClientInfo:[User=null, Host=null, application=null] - DDMUser ------------------------------------------------------------- Original statement: SELECT * FROM HR.EMPLOYEES Replaced by: SELECT substr("EMPLOYEES"."EMPLOYEE_ID",1,2) "EMPLOYEE_ID" , substr("EMPLOYEES"."FIRST_NAME",1,2) "FIRST_NAME" , substr("EMPLOYEES"."LAST_NAME",1,2) "LAST_NAME" , substr("EMPLOYEES"."EMAIL",1,2) "EMAIL" , substr("EMPLOYEES"."PHONE_NUMBER",1,2) "PHONE_NUMBER" , substr("EMPLOYEES"."HIRE_DATE",1,2) "HIRE_DATE" , substr("EMPLOYEES"."JOB_ID",1,2) "JOB_ID" , substr("EMPLOYEES"."SALARY",1,2) "SALARY" , substr("EMPLOYEES"."COMMISSION_PCT",1,2) "COMMISSION_PCT" , substr("EMPLOYEES"."MANAGER_ID",1,2) "MANAGER_ID" , substr("EMPLOYEES"."DEPARTMENT_ID",1,2) "DEPARTMENT_ID" FROM HR . EMPLOYEES
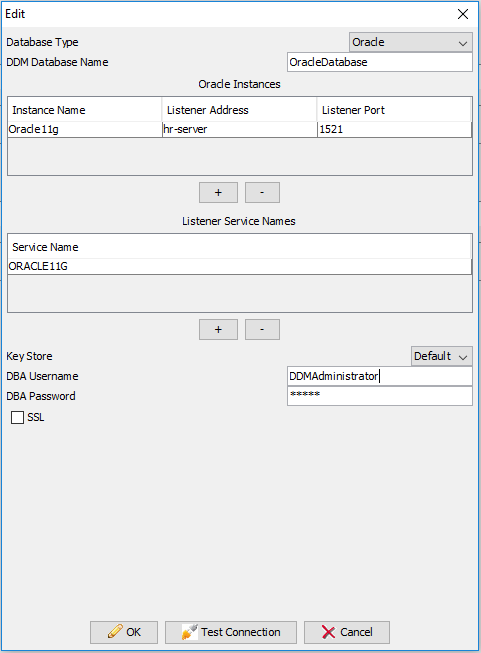
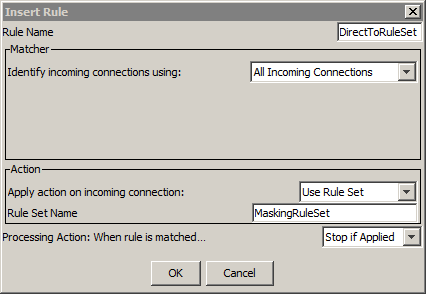
Database set to: OracleDatabase FolderAction: trying: MaskingRule for: [] MaskingRule.match: matcher: AnyMatcher h: [] Applying rule: MaskingRule MaskingAction.execute: SELECT * FROM HR.EMPLOYEES OracleDatabase: Getting connection for: DDMAdministrator OracleDatabase.buildURL: Finished being built URLjdbc:informatica:oracle://hr-server;ServiceName=Oracle11g OracleDatabase: Is Setting schema: true Try and impersonate using: user=DDMAdministrator and null catalog. Starting to impersonate user: DDMAdministrator -- Null catalog Adding for execution SQL statement: ALTER SESSION SET CURRENT_SCHEMA = DDMAdministrator Here are the 1 return codes after executing the statement list:- 0: Statement returned with number of rows: 0 Completed impersonation to user: DDMAdministrator Completed successfully impersonating user: DDMAdministrator -- Null catalog MaskingAction: Alias set is: ["EMPLOYEES"] OracleDatabase: Impersonating OracleDatabase: Getting connection for admin user = DDMAdministrator OracleDatabase: Getting connection for ddm admin user and password OracleDatabaseUser = DDMAdministrator ; Password = GCMNFIENGEBPNCBI OracleDatabaseAbout to obtain non-pooled connection. OracleDatabase.buildURL: Finished being built URLjdbc:informatica:oracle://hr-server;ServiceName=Oracle11g OracleDatabaseObtained connection successfully. OracleDatabase: Using ddm admin user DDMAdministrator, testing if impersonating supported for: client user = DDMUser ;client catalog = null ;client path = null OracleDatabase: Using ddm admin user DDMAdministrator, impersonating supported for: client user = DDMUser ;client catalog = null ;client path = null Try and impersonate using: user=DDMUser and null catalog. Starting to impersonate user: DDMUser -- Null catalog Adding for execution SQL statement: ALTER SESSION SET CURRENT_SCHEMA = DDMUser Here are the 1 return codes after executing the statement list:- 0: Statement returned with number of rows: 0 Completed impersonation to user: DDMUser Completed successfully impersonating user: DDMUser -- Null catalog MaskingAction: Rewriting start to: SELECT "EMPLOYEES" . "EMPLOYEE_ID" , "EMPLOYEES" . "FIRST_NAME" , "EMPLOYEES" . "LAST_NAME" , "EMPLOYEES" . "EMAIL" , "EMPLOYEES" . "PHONE_NUMBER" , "EMPLOYEES" . "HIRE_DATE" , "EMPLOYEES" . "JOB_ID" , "EMPLOYEES" . "SALARY" , "EMPLOYEES" . "COMMISSION_PCT" , "EMPLOYEES" . "MANAGER_ID" , "EMPLOYEES" . "DEPARTMENT_ID" FROM HR . EMPLOYEES Replace Using MaskingRule Original Statement: SELECT * FROM HR.EMPLOYEES Replaced by: SELECT substr("EMPLOYEES"."EMPLOYEE_ID",1,2) "EMPLOYEE_ID" , substr("EMPLOYEES"."FIRST_NAME",1,2) "FIRST_NAME" , substr("EMPLOYEES"."LAST_NAME",1,2) "LAST_NAME" , substr("EMPLOYEES"."EMAIL",1,2) "EMAIL" , substr("EMPLOYEES"."PHONE_NUMBER",1,2) "PHONE_NUMBER" , substr("EMPLOYEES"."HIRE_DATE",1,2) "HIRE_DATE" , substr("EMPLOYEES"."JOB_ID",1,2) "JOB_ID" , substr("EMPLOYEES"."SALARY",1,2) "SALARY" , substr("EMPLOYEES"."COMMISSION_PCT",1,2) "COMMISSION_PCT" , substr("EMPLOYEES"."MANAGER_ID",1,2) "MANAGER_ID" , substr("EMPLOYEES"."DEPARTMENT_ID",1,2) "DEPARTMENT_ID" FROM HR . EMPLOYEES Done by ClientInfo:[User=null, Host=null, application=null] - DDMUser FolderAction: rule matched: true FolderAction: rule applied: true DNRStatementProcessor.getStatementHandler: rule match: [] on: SELECT * FROM HR.EMPLOYEES ------------------------------------------------------------- Original statement: SELECT * FROM HR.EMPLOYEES Replaced by: SELECT substr("EMPLOYEES"."EMPLOYEE_ID",1,2) "EMPLOYEE_ID" , substr("EMPLOYEES"."FIRST_NAME",1,2) "FIRST_NAME" , substr("EMPLOYEES"."LAST_NAME",1,2) "LAST_NAME" , substr("EMPLOYEES"."EMAIL",1,2) "EMAIL" , substr("EMPLOYEES"."PHONE_NUMBER",1,2) "PHONE_NUMBER" , substr("EMPLOYEES"."HIRE_DATE",1,2) "HIRE_DATE" , substr("EMPLOYEES"."JOB_ID",1,2) "JOB_ID" , substr("EMPLOYEES"."SALARY",1,2) "SALARY" , substr("EMPLOYEES"."COMMISSION_PCT",1,2) "COMMISSION_PCT" , substr("EMPLOYEES"."MANAGER_ID",1,2) "MANAGER_ID" , substr("EMPLOYEES"."DEPARTMENT_ID",1,2) "DEPARTMENT_ID" FROM HR . EMPLOYEES