Dynamic Data Masking
- Dynamic Data Masking 9.9.1
- All Products


Preferred Store
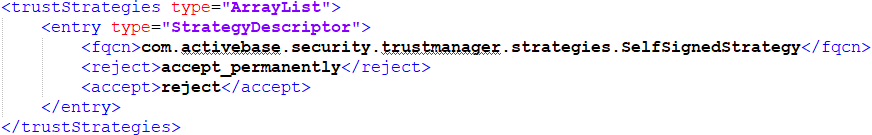
| Trust Strategy Result
| Client Connection
| Action
|
|---|---|---|---|
set
| Accept permanently
| Allow
| Dynamic Data Masking permanently stores the new certificate and uses it for the duration of the current and all future sessions.
|
set
| Accept temporarily
| Allow
| Dynamic Data Masking temporarily accepts the new certificate and uses it for the duration of the current session.
|
not set
| Accept permanently
| Allow
| Dynamic Data Masking temporarily accepts the new certificate and uses it for the duration of the current session.
|
not set
| Accept temporarily
| Allow
| Dynamic Data Masking temporarily accepts the new certificate and uses it for the duration of the current session.
|
set
| Reject
| Refuse
| No action taken.
|
not set
| Reject
| Refuse
| No action taken.
|
not set
| -
| Refuse
| No action taken.
|
set
| -
| Refuse
| No action taken.
|
