Dynamic Data Masking
- Dynamic Data Masking 9.9.4
- All Products

Dynamic Data Masking Server
| Administrative Tools
| ||
|---|---|---|---|
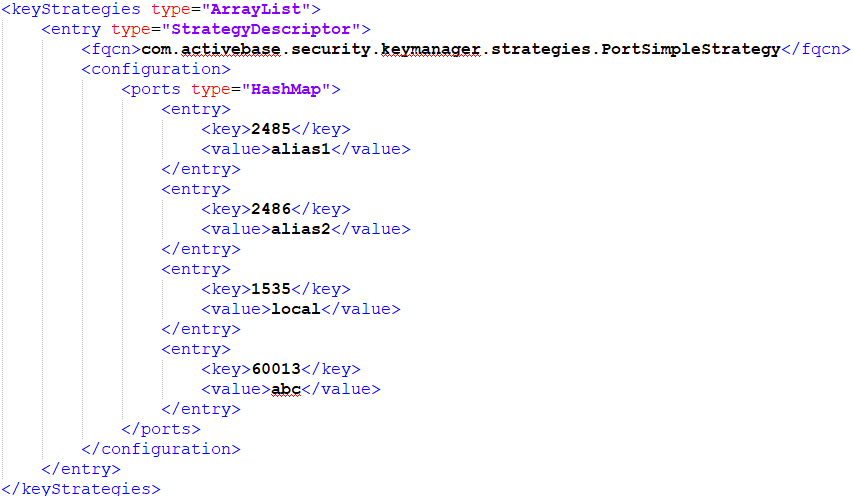
Keystore or Keystores
| Dynanic Data Masking Server SSL Functionality
| Truststore or Truststores
| Dynamic Data Masking Administrative Tools SSL Functionality
|
not set
| Provides the self-signed certificate to the SSL client. The key strategy is not relevant.
| not set
| Accepts any certificate. Can connect.
|
set with certificates
| Provides to SSL client:
| not set
| Accepts any certificate. Can connect.
|
not set
| Provides the self-signed certificate to SSL client. Key strategy is not relevant.
| set with certificates
| Cannot connect, because the Dynamic Data Masking Server has no matching private key.
|
set with certificates
| Must have a configured port strategy. Provides to SSL client a signed certificate associated with an alias mapped to a specific SSL port.
| set with certificates
| Can connect, but the Dynamic Data Masking Server must have matching private key.
|