Dynamic Data Masking
- Dynamic Data Masking 9.9
- All Products

Scenario
| Configured Protocols
| Runtime Protocols
| ||
|---|---|---|---|---|
Global
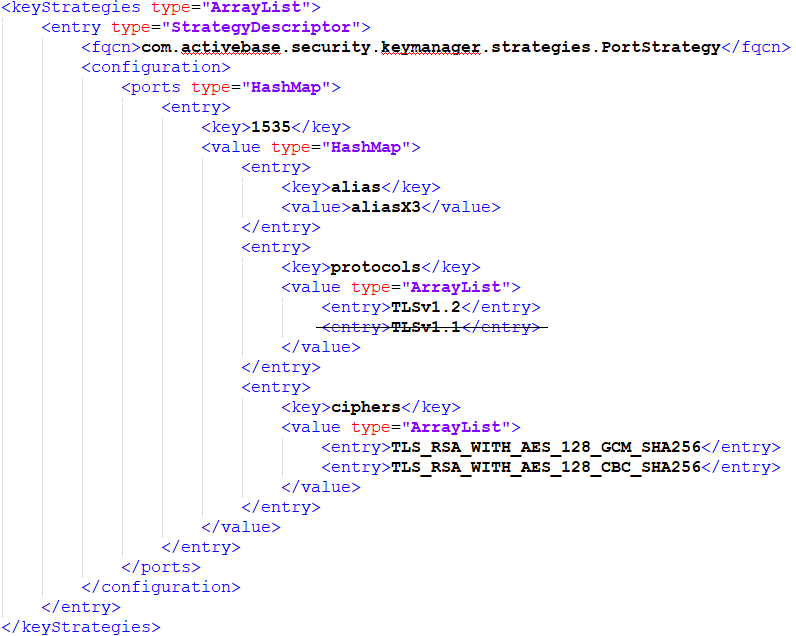
| Strategy on Port 1535
| Port to Communicate With
| Port to Communicate With
| |
Client (1535)
| Database
| |||
1
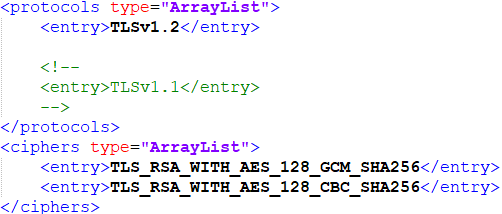
| TLSv1.2
TLSv1.1
| TLSv1.2
| TLSv1.2
| TLSv1.2 TLSv1.1
|
2
| TLSv1.2
| TLSv1.2
TLSv1.1
| TLSv1.2 TLSv1.1
| TLSv1.2
|
3
| TLSv1.2
TLSv1.1
| Not set
| TLSv1.2 TLSv1.1
| TLSv1.2 TLSv1.1
|
4
| Not set
| TLSv1.2
TLSv1.1
| TLSv1.2 TLSv1.1
| all protocols
|
5
| Not set
| Not set
| all protocols
| all protocols
|
server network protocols 10.40.1.172:1535 server network ciphers 1535