Data Engineering Integration
- Data Engineering Integration 10.5.2
- All Products

Vehicle registration expired
Dear Arianne Fitzgerald, Vehicle # 1B3HB48B67D562726 in your possession has the issue: Vehicle registration expired. Please resolve the issue in 10 days.
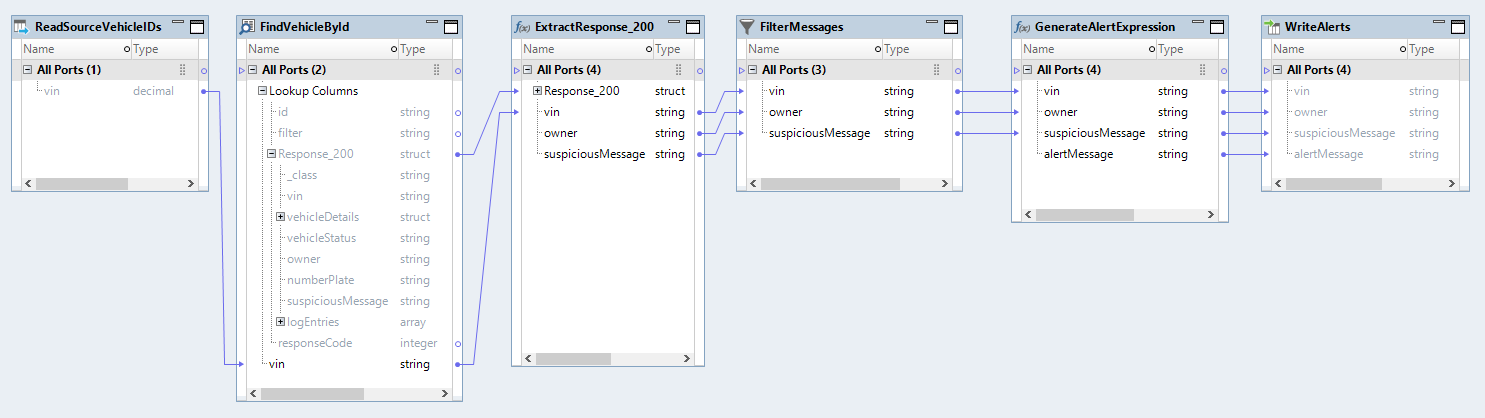
/org.company/vehicles/{id}
id = vin
Response_200.owner
Response_200.suspiciousMessage
suspiciousMessage != NULL
'Dear ' || owner || ', Vehicle # ' || vin || ' in your possession has the issue: ' || suspiciousMessage || '. Please resolve the issue in 10 days.'