PowerCenter
- PowerCenter 10.5.4
- All Products

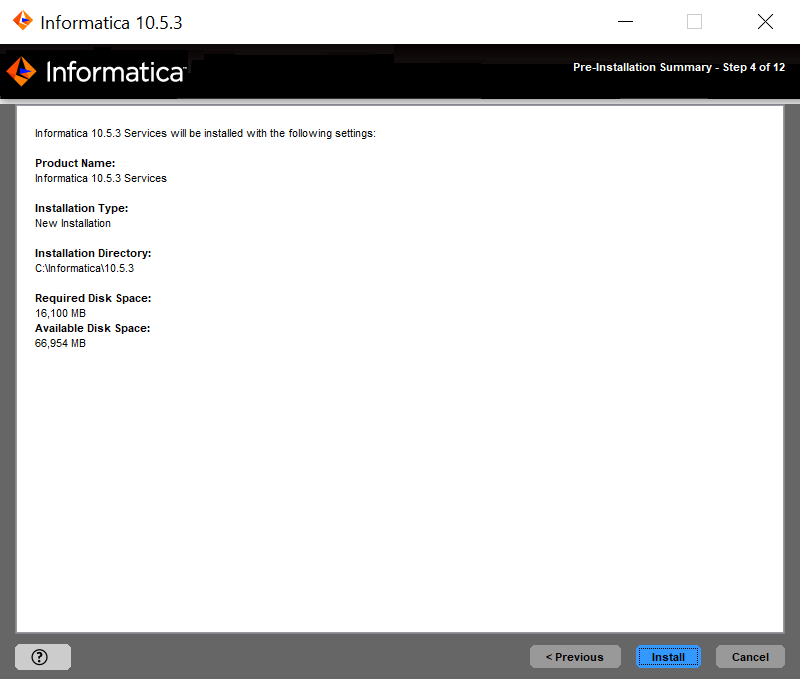
Property
| Description
|
|---|---|
Enable HTTPS for Informatica Administrator
| Select this option to secure the connection to Informatica Administrator. To use an unsecure HTTP connection, clear the option.
By default, if secure communication is enabled for the domain, the installer enables this option. You can also enable this option even if you do not enable secure communication for the domain.
|
Port
| The port to use for communication between Informatica Administrator and the Service Manager.
|
Use a keystore file generated by the installer
| Use a self-signed keystore file generated by the installer. The installer creates a keystore file named Default.keystore in the following location:
<Informatica installation directory>\tomcat\conf\
|
Specify a keystore file and password
| Use a keystore file that you create. You can use a keystore file with a self-signed certificate or a certificate signed by a certification authority.
|
Keystore password
| A plain-text password for the keystore file. Required if you use a keystore file that you create.
|
Keystore file
| Path and file name of the keystore file. Required if you use a keystore file that you create.
|
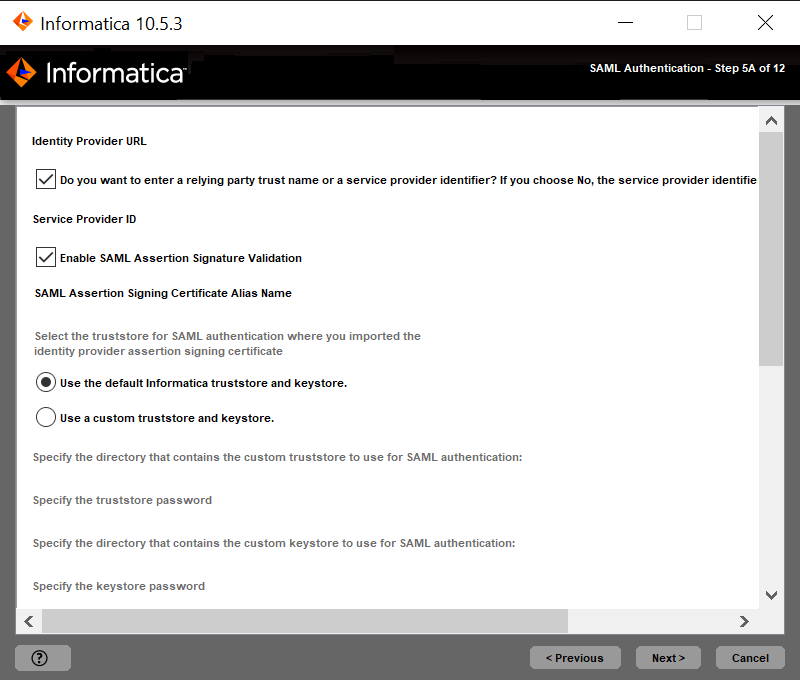
Option
| Description
|
|---|---|
Use the default Informatica SSL certificate file.
| Select to use the default Informatica truststore file for SAML authentication.
|
Enter the location of the SSL certificate file.
| Select to use a custom truststore file for SAML authentication. Specify the directory containing the custom truststore file on gateway nodes within the domain. Specify the directory only, not the full path to the file.
|
Property
| Description
|
|---|---|
Truststore Directory
| Specify the directory containing the custom truststore file on gateway nodes within the domain. Specify the directory only, not the full path to the file.
|
Truststore Password
| The password for the custom truststore file.
|
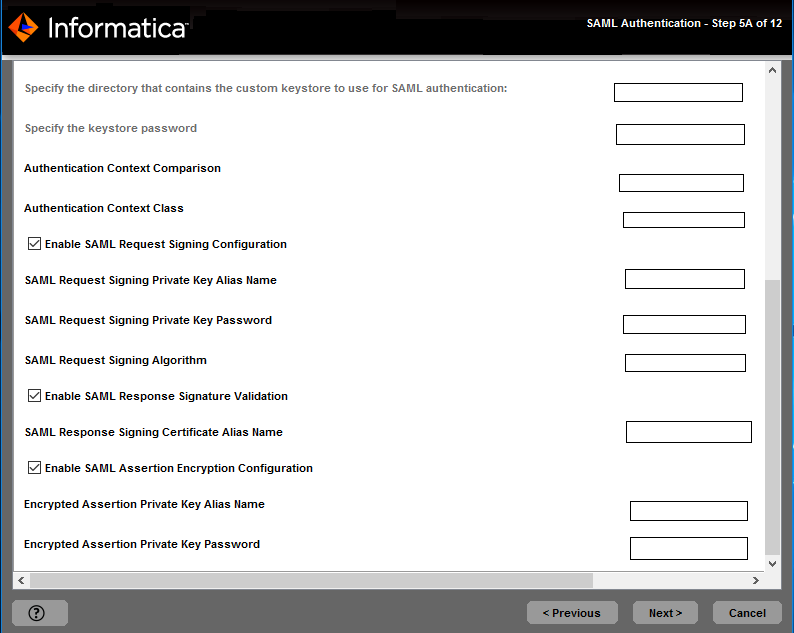
Keystore Directory
| Specify the directory containing the custom keystore file.
|
Keystore Password
| The password for the custom keystore file.
|