Application Integration
- Application Integration
- All Products


GET <Informatica Intelligent Cloud Services URL>/active-bpel/rt/<API unique name> Accept: application/json Authorization: Basic Auth username: <Informatica Intelligent Cloud Services user name> password: <Informatica Intelligent Cloud Services password>
GET <Informatica Intelligent Cloud Services URL>/active-bpel/rt/<API unique name> Accept: application/json IDS-SESSION-ID: <sessionId>
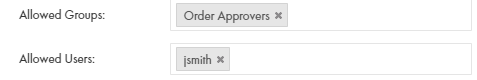
GET <Informatica Intelligent Cloud Services URL>/active-bpel/rt/<API unique name> Accept: application/json Authorization: Basic Auth username: <Informatica Intelligent Cloud Services user name> password: <Informatica Intelligent Cloud Services password>
GET <Informatica Intelligent Cloud Services URL>/active-bpel/rt/<API unique name> Accept: application/json IDS-SESSION-ID: <sessionId>