Data Integration
- Data Integration
- All Products

Field
| Description
|
|---|---|
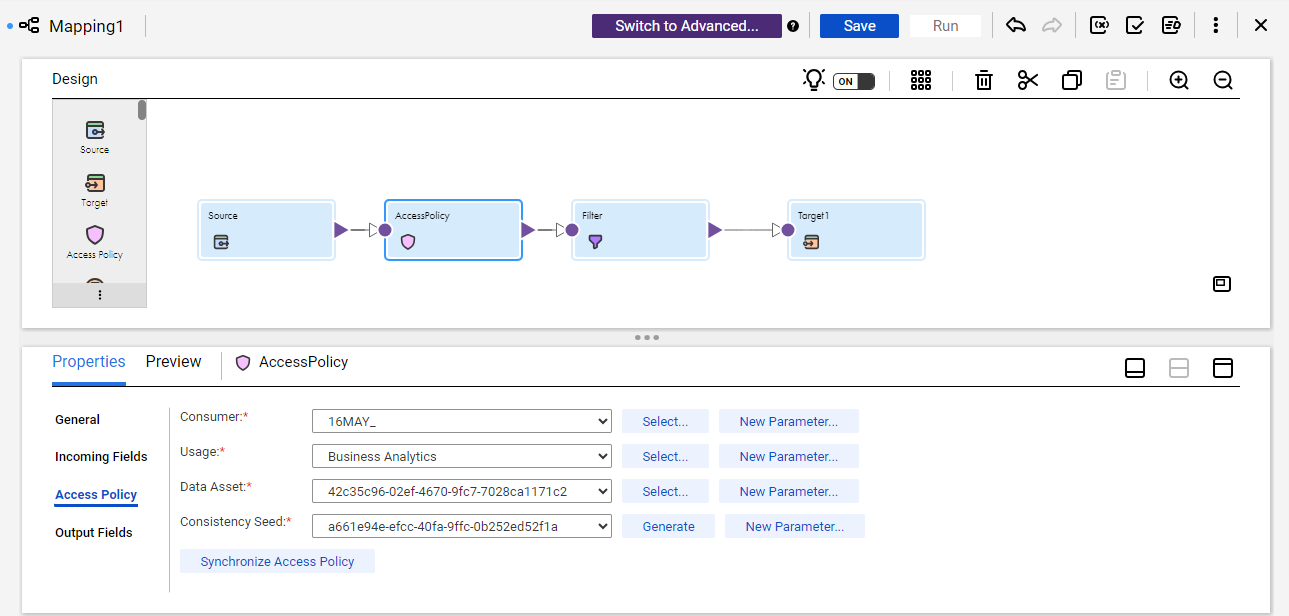
Consumer
| Identifies the user who will consume the data. Select a single user.
Active users in your organization with the Data Marketplace User role appear in this list. Select one of those users. Note that the user you choose helps determine the set of rules that the transformation applies to the data.
|
Usage
| Identifies the usage context such as for customer analysis or anti-money laundering research. Usage context is one type of metadata that helps determine the set of rules that the transformation applies to the data.
Users create and manage usage contexts in Data Marketplace . To learn more, see Set Up Data
Marketplace in the Data Marketplace help. |
Data Asset
| Identifies the data asset to which the transformation applies the rules.
A data asset is a data structure such as a table in a database that you have cataloged in
Data Governance and Catalog .
By default, the source object that you selected when you configured the Source transformation appears when you click
Select . Select the data asset in that source object.
Alternatively, you can select a new connection and a new data asset.
Select
Override Asset name if there is a difference between the table name and the asset name in the data catalog.
|
Consistency Seed
| Provides a value that represents the rule logic that the transformation applies to the data
element classification. A consistency seed ensures that a rule's behavior for a data element classification will be
consistent for the same consistency seed value, usage context, and
user across mappings. For example, you can ensure that a rule always
replaces the last name "Smith" with "Abcd." If you want consistent tokenization between different Access Policy transformations, insert the same consistency seed in other Access Policy transformations. If you don't want consistent tokenization between different Access Policy transformations, generate a unique seed.
|